Operation Midnight Hammer: Mastering Deception in Warfare and Cybersecurity
Operation Midnight Hammer’s success in striking Iran’s nuclear sites in June 2025 stands as a testament to the power of deception—both on the battlefield and in cyberspace. The U.S. military’s intricate campaign of misdirection was crucial in ensuring tactical surprise and operational success, and it offers a fascinating parallel to the cutting-edge strategies used by cybersecurity innovators like Deceptive Bytes.
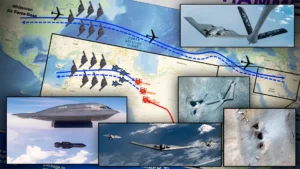
The Art of Deception in Operation Midnight Hammer
The operation’s planning was a masterclass in strategic deception. As the main B-2 bomber strike group quietly flew east toward Iran, a separate group of bombers headed toward the Pacific, serving as a decoy to mislead Iranian intelligence about the true direction of the attack. This ruse, known only to a handful of planners, was complemented by minimal communications and the use of advanced stealth technology. Just before entering Iranian airspace, the U.S. also launched Tomahawk cruise missiles from a submarine, further confusing Iranian radar operators and diverting attention from the main aerial assault.
The Trump administration’s role in this deception was pivotal. In the days leading up to the strike, President Trump publicly projected an image of indecision, stating that he would wait two weeks before making any determination about bombing Iran—a statement designed to lull both Iranian leaders and the international community into a false sense of security. Behind the scenes, however, Trump had already resolved to carry out the attack, and military preparations were well underway. This political misdirection was reinforced by Trump’s public lunch with a known opponent of military action, further fueling speculation that he might hold off. In reality, less than 30 hours after these statements, he authorized the assault. This deliberate confusion bought precious time for military planners and ensured the element of surprise, allowing the U.S. to execute a complex and highly secretive operation that caught Iran—and much of the world—completely off guard.
Endpoint Deception: The Cybersecurity Parallel
This military deception mirrors the proactive strategies employed in cybersecurity, particularly by companies like Deceptive Bytes. However, while traditional cyber deception often relies on decoys or honeypots, Deceptive Bytes takes a more sophisticated approach: endpoint deception. Rather than setting traps, their technology dynamically creates false information about the actual environment on endpoints. This distorts the perception of ransomware and other malicious actors, confusing them about the true nature of the system they are targeting.
By altering the environment’s apparent characteristics in real time, Deceptive Bytes prevents attackers from accurately mapping or exploiting the system. This not only stops malware and ransomware before they can execute but also reduces the attack surface and improves overall security posture. Attackers are forced to waste resources and often reveal their presence early in the attack chain, giving defenders a critical advantage.
Deception as a Force Multiplier
Just as Operation Midnight Hammer’s decoys and misdirection enabled the U.S. to strike with minimal resistance, Deceptive Bytes’ endpoint deception tactics force cyber attackers to question every move, undermining their confidence and effectiveness. Both strategies demonstrate that in modern warfare—whether kinetic or digital—deception is a powerful tool for gaining the upper hand, neutralizing threats, and protecting critical assets. In a world where the element of surprise can mean the difference between victory and defeat, mastering the art of deception remains as vital as ever.
Don’t Miss a Thing
Sign up today and we’ll send an email when new posts come out.
We collect and use this information in accordance with our privacy policy.


